Inbound IP Rules
Allow incoming connections only from specified IP ranges.
You can configure which IP addresses can connect to your Render services over the public internet:
By setting these inbound IP rules, you can grant access only to IP ranges you trust.
All workspaces can set inbound IP rules for:
- Individual Render Postgres and Key Value datastores
Enterprise orgs can also set rules for:
- Individual web services and static sites
- An entire environment
- An entire workspace
After you set IP rules, Render only allows inbound service connections from the IP ranges you specify. Disallowed IPs are automatically blocked with a 403 Forbidden response.
Requests are blocked at the edge and do not reach your service. For web services, blocked requests do still appear in HTTP request logs.
Inbound IP rules apply only to connections from the public internet.
These rules do not apply to inter-service communication over your private network. For private network controls, see Blocking cross-environment traffic.
Setup
Render Postgres / Key Value
All workspaces can set inbound IP rules for Render Postgres and Key Value. See the documentation for each type of managed datastore:
All other resource types
Setting IP rules for any resource besides a managed datastore requires an Enterprise org.
Follow these steps to set inbound IP rules for a web service, static site, environment, or workspace.
-
In the Render Dashboard, open the settings page for the service or environment you want to configure.
- For workspace-level rules, click Network Access in the left pane of your workspace home.
-
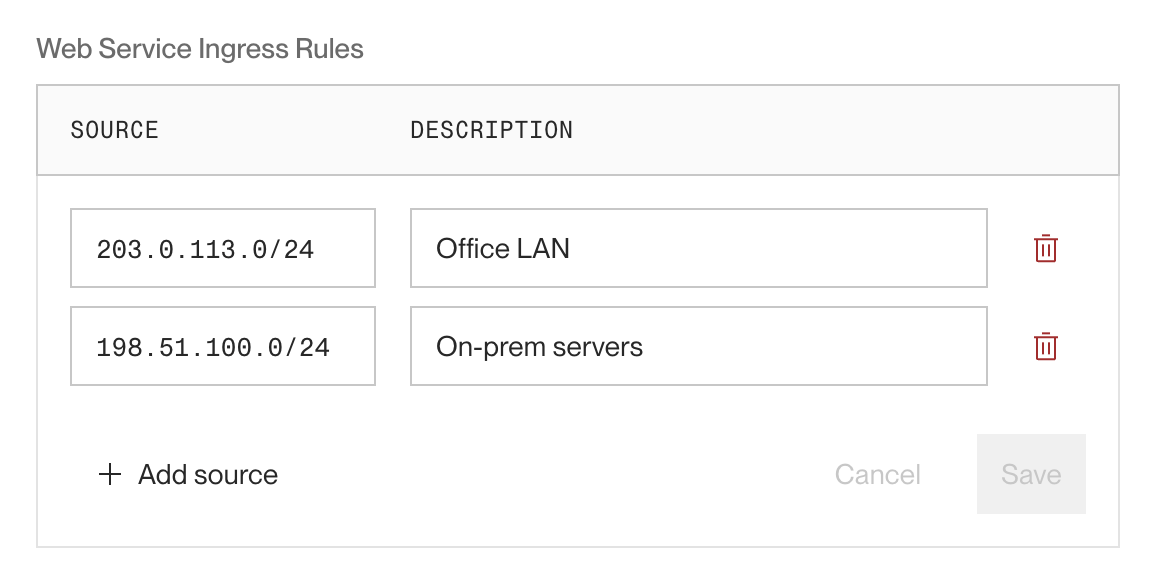
Scroll down to the Networking section and find Inbound IP Restrictions:
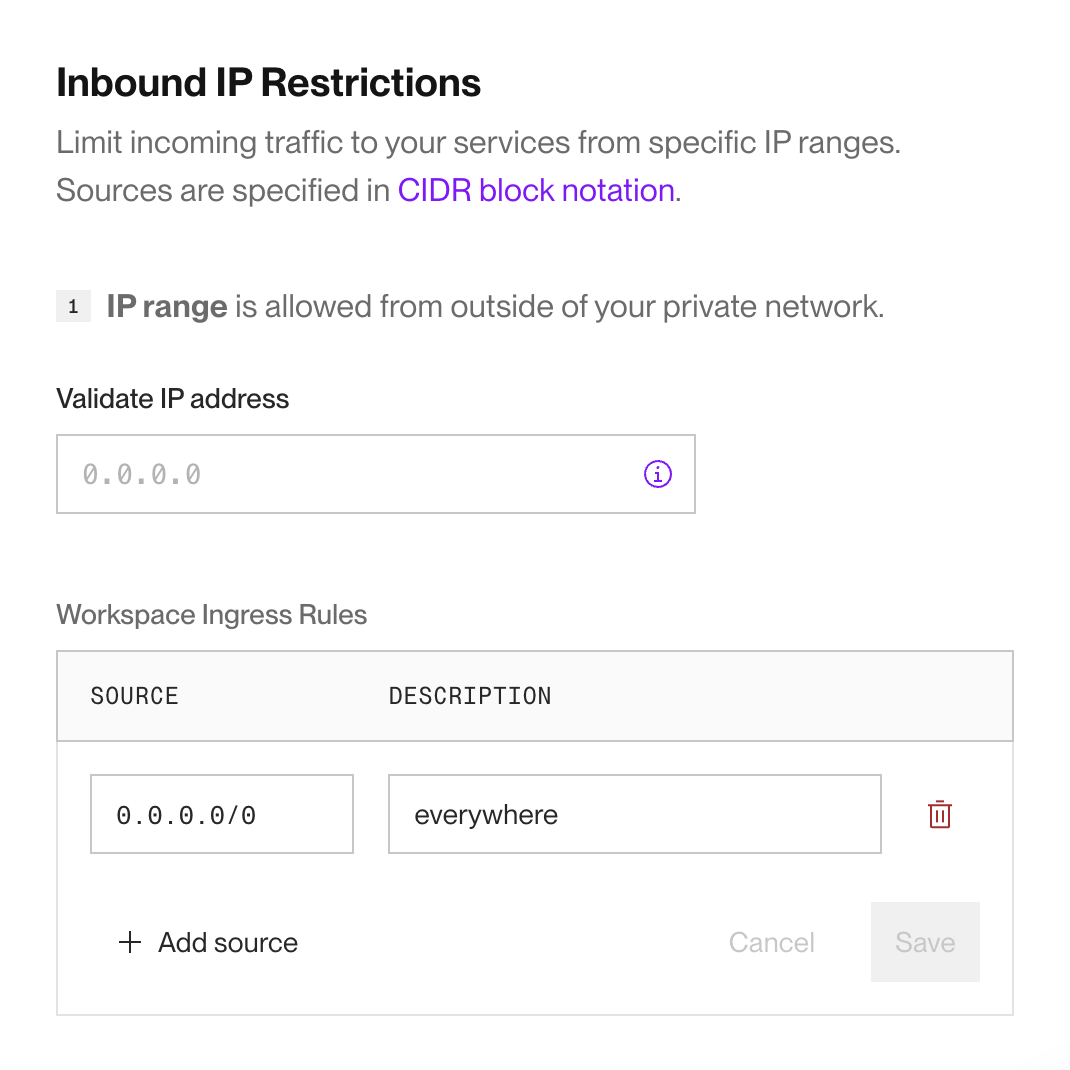
If you haven't made any changes yet, you'll see a single default rule:
0.0.0.0/0(allow all IPs). -
Click an existing rule to edit it, or click + Add source to create a new rule. You can also click the trash icon next to a rule to delete it.
- Learn more about rule format below.
If you delete all rules, Render blocks all inbound traffic to the affected service(s)!
-
Click Save to apply your changes.
You're all set! Your new rules take effect within a few seconds.
Rule format
Inbound IP rules are allowlists of IP ranges you specify using CIDR notation. Render allows connections from the IP ranges you specify and blocks connections from all other IPs.
Only IPv4 CIDR ranges are supported.
Here are some example ranges:
| Rule | Meaning |
|---|---|
|
|
Allow any IP address. This is the default rule for services besides Render Key Value instances. |
|
|
Allow IP addresses This might represent a company's office network or a trusted third-party service. |
|
|
Allow IP addresses This smaller range of 8 addresses might represent a specific subnet of an office network. |
|
|
Allow only the IP address The |
Combining IP rules
This section applies only to Enterprise orgs.
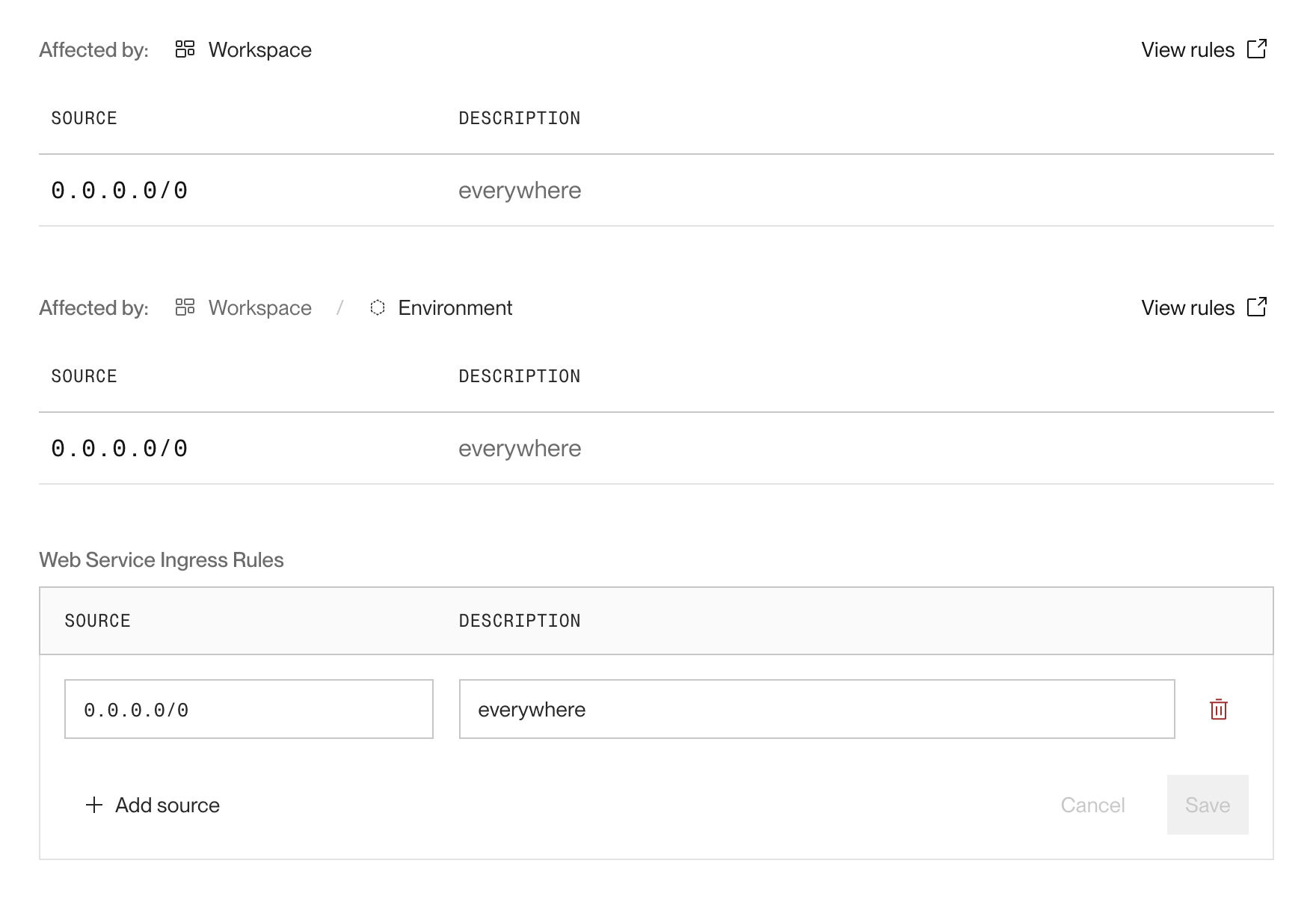
When a service is subject to IP rules at multiple levels (workspace, environment, and/or service), an inbound IP must be allowed by each level's rules to successfully connect:
If an IP is allowed at the service level but disallowed at the environment level (or vice versa), the connection is blocked.
When you view a service's inbound IP rules, you can see each level of rules that apply to it:
FAQ
Can I set IP rules for a private service / background worker / cron job?
No. These service types never receive traffic from the public internet.
How do I allow connections from all IP addresses?
Include the value 0.0.0.0/0 (CIDR notation for "any IPv4 address") in your inbound IP rules.
This is the default rule for services besides Render Key Value instances.
What happens if I delete all rules for a given resource?
If you delete all inbound IP rules for a given service, environment, or workspace, Render blocks all inbound traffic to the affected service(s).
Why don't I see inbound IP rule settings for my web service?
Inbound IP rules require an Enterprise org for everything besides managed datastores.